Overview
Burp Suite is a Java application that can be used to secure or penetrate web applications. It comes pre-installed on Kali Linux and ParrotOS, however can be installed on your operating system of choice via the community edition download on their website. The suite consists of different tools, such as:
- Spider: Crawls target web applications in an attempt to map functionalities and potential vulnerabilities.
- Proxy: Intercepts traffic between the attacking and target system and allows for the content of requests and responses to be altered while in transit.
- Intruder: Allows input fuzzing for proxied traffic. Common uses include brute-forcing directories and credentials.
- Repeater: Allows for requests to be manually altered and forwarded to the web app.
- Sequencer: An entropy checker that checks for the randomness of tokens generated by the webserver. These tokens are generally used for authentication in sensitive operations: cookies and anti-CSRF tokens are examples of such tokens.
- Decoder: Lists the common encoding methods like URL, HTML, Base64, Hex, etc. This tool comes handy when looking for chunks of data in values of parameters or headers. It is also used for payload construction for various vulnerability classes.
- Scanner: Not available in the community edition, however it scans website for vulnerabilities.
| Tool Name | Version | MITRE ATT&CK Tactic | MITRE ATT&CK Technique |
|---|---|---|---|
| Burpsuite Community Edition | V2022.8.4 | Credential Access | Brute Force |
Setting the Browser to Proxy Traffic
The web browser must first be configured to proxy traffic to Burp in order to intercept traffic. The below example shows the configuration for the Mozilla Plugin FoxyProxy.
- Download and install FoxyProxy from
https://getfoxyproxy.org/. - Create a new proxy profile, set the Proxy IP address to
127.0.0.1and the port to8080. - Enable the proxy in the web browser to allow Burpsuite to intercept the traffic.
- Open Burpsuite and navigate to the Proxy Tab, select the sub-tab Intercept and enable Interception via the Intercept is off button.
Burpsuite proxy settings can be amended via the Proxy tab, Options sub-tab under the Proxy Listeners section.
Brute Forcing WebApp Credentials
To brute force potential credentials for a webapp, Burpsuite can be used to fuzz username and password fields.
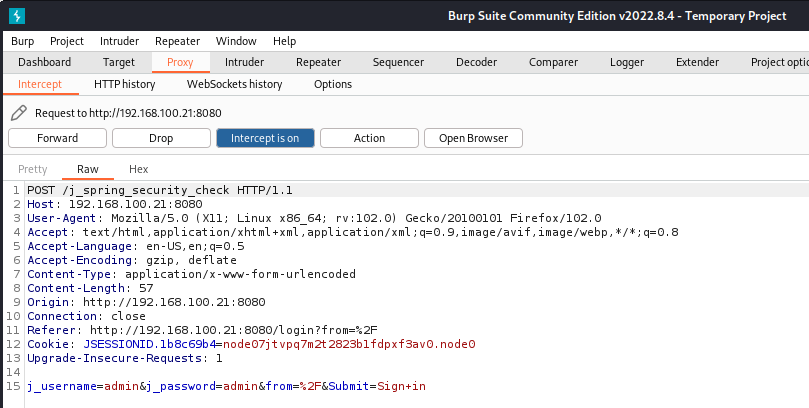
With Burpsuite intercepting traffic, attempt to enter credentials (application defaults are always a good start). In the example below the request has been intercepted and shows two fields of interest,
j_usernameandj_passwordwhich can be fuzzed.![Burpsuite Fuzzing - Fields Burpsuite Fuzzing - Fields]()
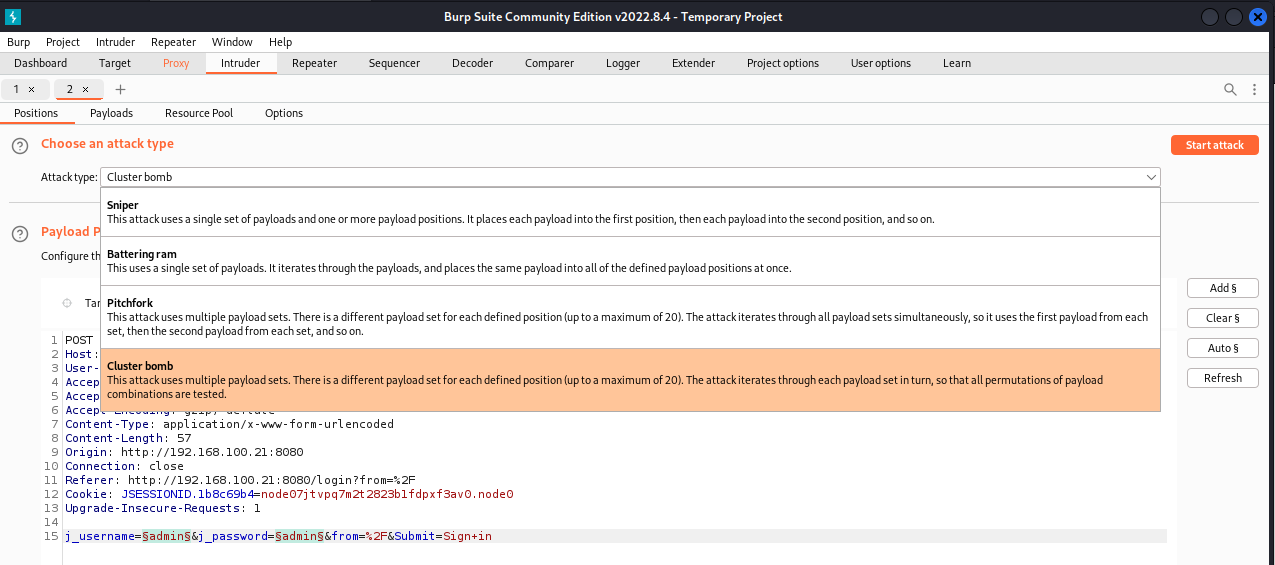
Send the request to the Intruder via right clicking in the Raw text box and selecting Send to Intruder or using the hotkey
Ctrl+I. Automatic detection of possible fields to fuzz will be detected, however in some cases will provide more fields than necessary. The automatic selections can be cleared and target fields added. The below shows fields for the username and password highlighted and the selections available for the attack type.![Burpsuite Fuzzing - Field Selection Burpsuite Fuzzing - Field Selection]()
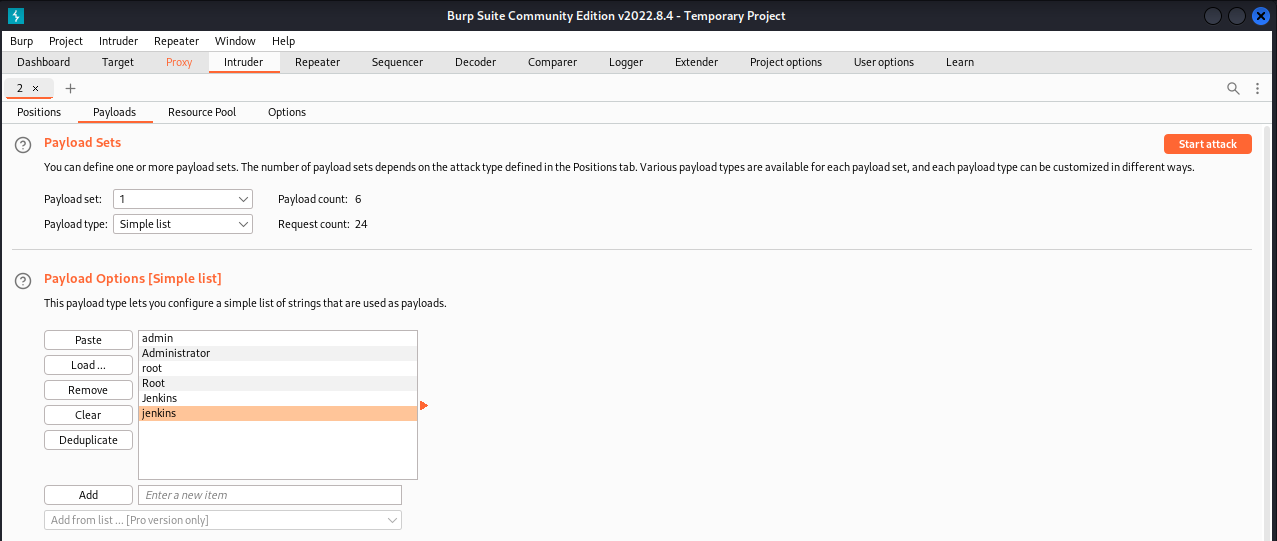
Select the Payloads sub-tab within Intruder, it will bring up the payload options where word lists or manual entries can be added for both of the selected username and password fields. Note that in the first section, Payload Sets, there is a dropdown selection for which payload set to updated. 1 is linked to the username and 2 is linked to the password selections from the step previous. In the below example, 6 usernames have been manually input along with a list of 4 potential passwords. As Cluster Bomb was selected as the attack type, each username and password combination will be attempted equaling a total of 24 requests.
![Burpsuite Fuzzing - Payload Burpsuite Fuzzing - Payload]()
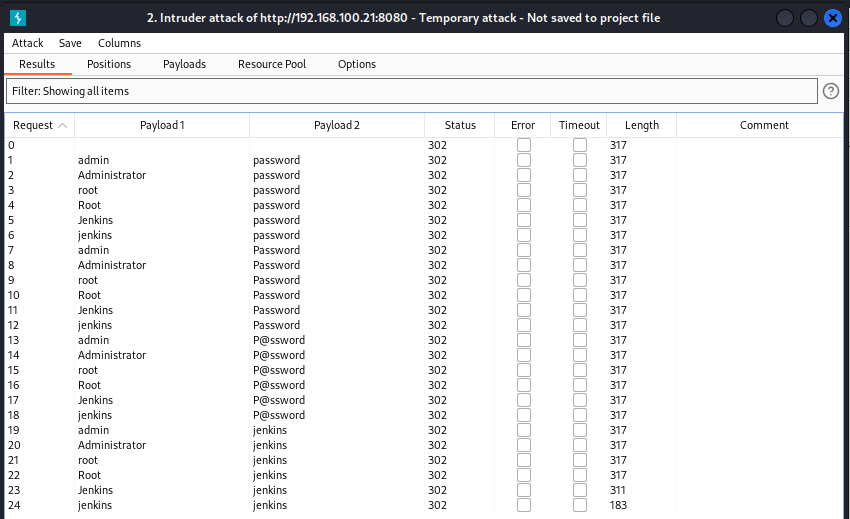
Click the Start Attack button, BurpSuite will begin to run through the lists and provide a running log of attempts. Take note of the output Status Codes and Response Lengths to highlight any potentially valid credentials. In the example below,
jenkins:jenkinswas an outlier, returning a different length response from the other attempts which could indicate that its a valid credential set.![Burpsuite Fuzzing - Output Burpsuite Fuzzing - Output]()