Overview
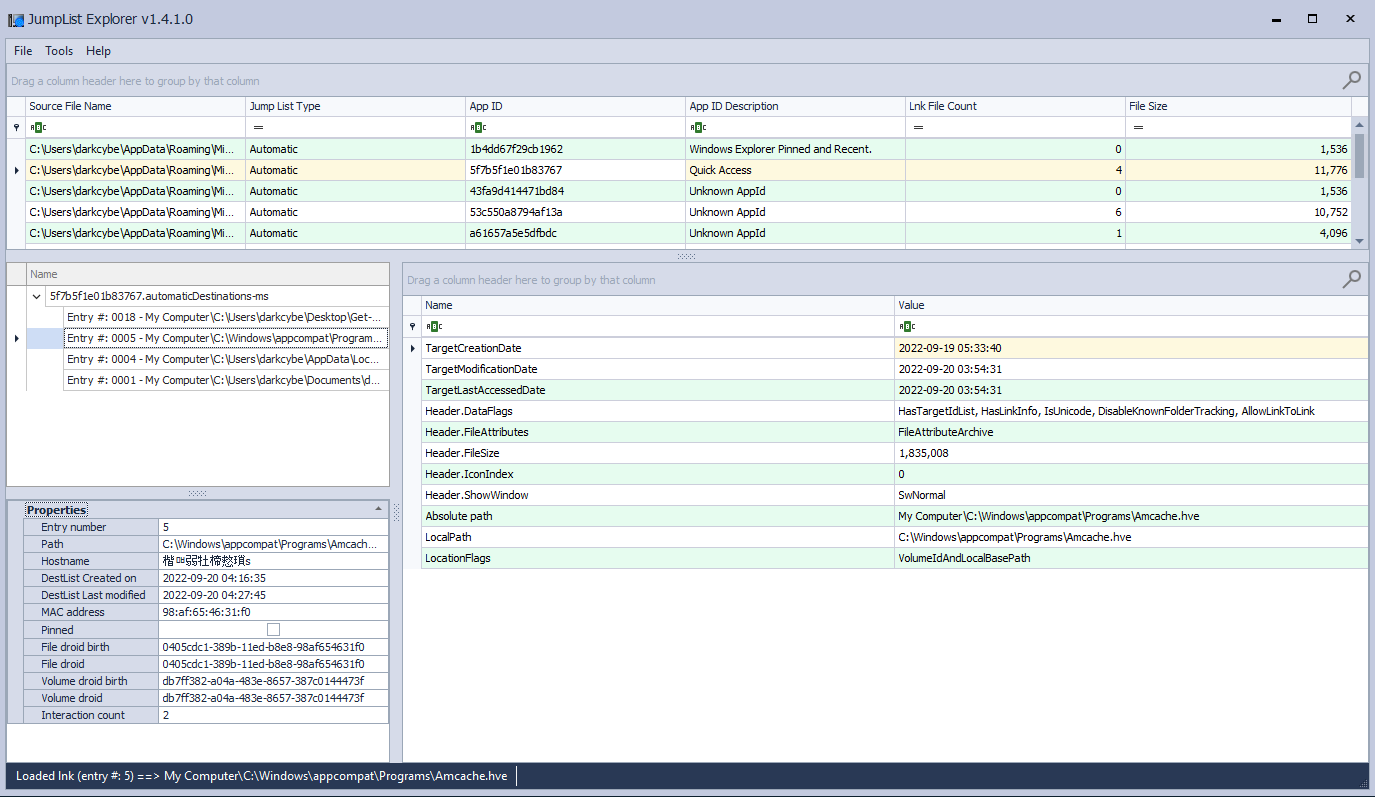
The JumpListExplorer (JLE) is a tool that parsers Windows AutomaticDestinations files to provide information relating to application execution. Results are recorded per application Id (AppID) and show folders and applications spawned via a parent application. Eric Zimmerman maintains a repository of common AppID mappings on his GitHub.
Parsing the Windows Jump List entries can aid forensic investigations by providing evidence of program execution and file and folder interaction activities. Further information about the Jump List can be found on the Evidence of Execution page.
There are two versions of the JLE available, a GUI and a Command Line parser.
| Tool Name | Version | MITRE ATT&CK Tactic | MITRE ATT&CK Technique |
|---|---|---|---|
| Jump List Explorer (JLE GUI) Jump List Explorer Cmd (JLECmd) | V1.4.1.0 | Execution |
Instructions
Loading AutomaticDestinations Files via JumpListExplorer
- Run JumpListExplorer, the application does not require Administrative permissions
- Select menu option File and Load Jump Lists, navigate to the directory containing the automaticDestinations files you wish to parse. If running the tool on a live system, automaticDestinations files are stored in the following directory by default
C:%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations - Select a single or multiple automaticDestinations files and select Open.
Output
Interesting Fields
- TargetCreationDate
- TargetModificationDate
- TargetLastAccessedDate
- LocalPath
- Interaction count