Overview
Registry Explorer allows Windows registry hives to be interrogated and parsed for a wide variety of forensic artifacts. The tool comes in two versions, a GUI and a commandline interface. Eric Zimmerman has created several plugins that allow automated parsing for certain forensic objects.
| Tool Name | Version | MITRE ATT&CK Tactic | MITRE ATT&CK Technique |
|---|---|---|---|
| Registry Explorer (RECmd) Registry Explorer (GUI) | V1.6.0.0 | Execution Persistence Defense Evasion Credential Access |
Instructions
Loading a Hosts Registry via Registry Explorer
- Run RegistryExplorer.exe as an Administrator if interrogating a live host
- Hive Selection
- Live Host: Navigate to menu option File and Live System and then select the desired registry hive
- Registry Dump: Navigate to menu option Load Hive and navigate to the desired registry hive via Explorer.
Hive details can be exported to several formats via the menu option File and Export
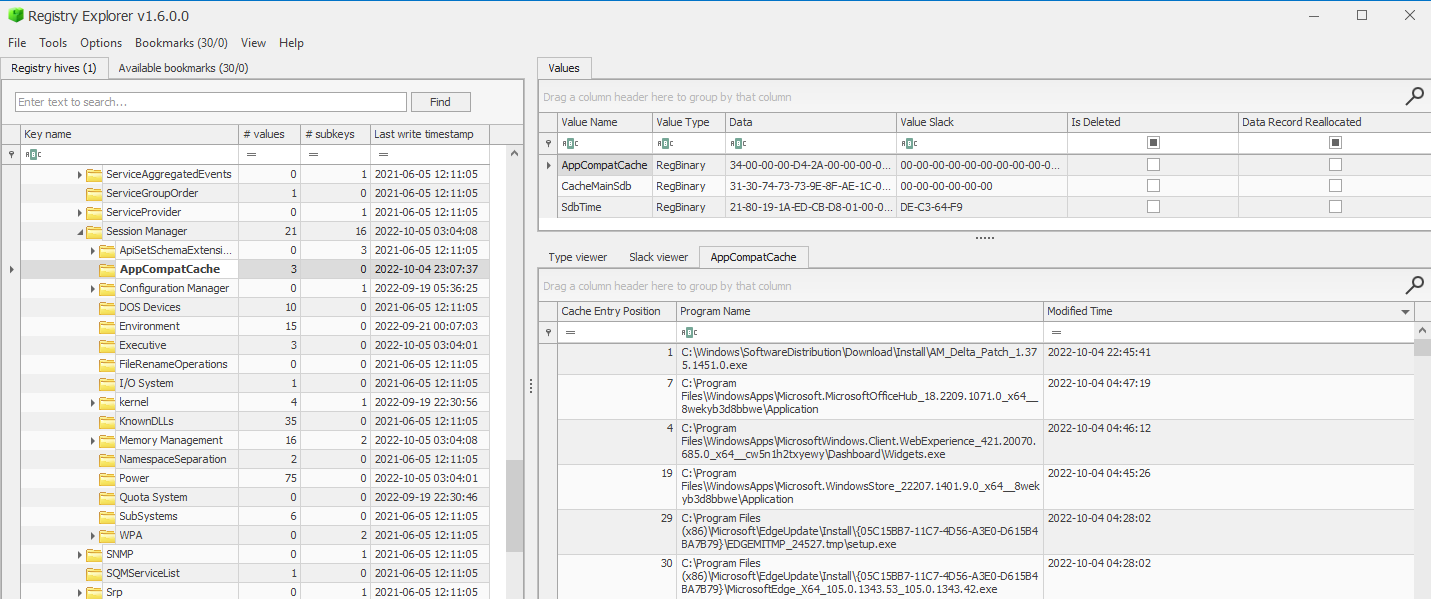
Parsing the AmCache.hve for Evidence of Execution
Interesting Keys
Root\- InventoryDeviceContainer: OS devices such as bluetooth, printers, etc. Has links to DevicePnps
- InventoryDevicePnP: Plug and Play (PnP) devices such as bluetooth, USB, etc. More verbose details than those contained in DeviceContainers
- InventoryDriverBinary: System Drivers
- InventoryDriverPackage: Package information that links to both DeviceContainers and DevicePnPs
- InventoryApplicationShortcut: .LNK files
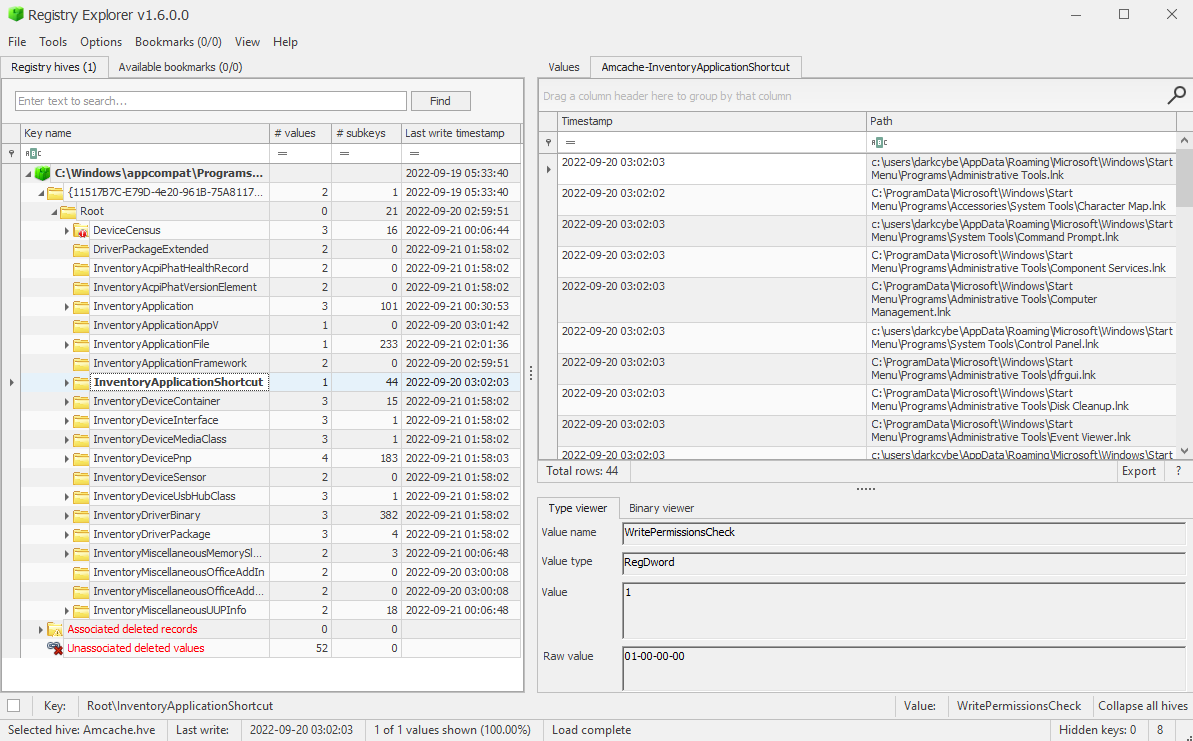
Parsing the BAM/DAM for Evidence of Execution
Execution Timeis a reference to the last execution time.
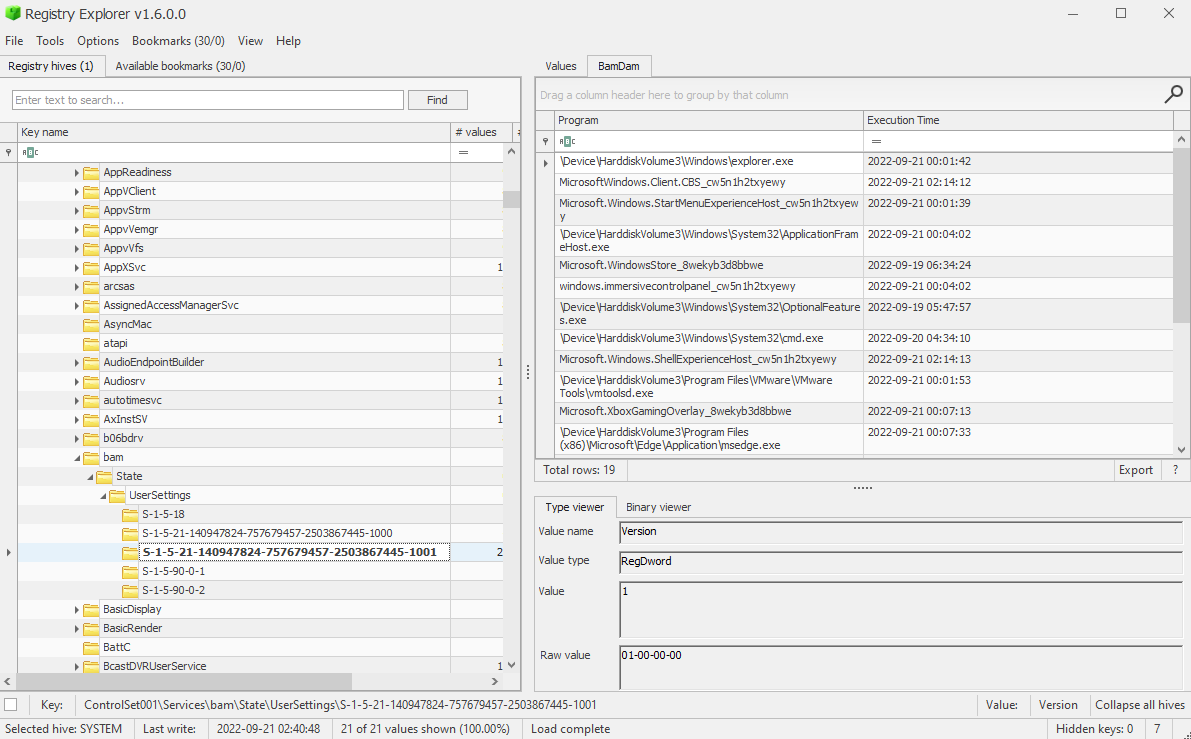
Parsing the LastVisitedMRU for Evidence of Execution
Interesting Fields
- Executable: Records the parent application
- Absolute Path: Records the file opened
- Opened On: Date-time-group of last access time
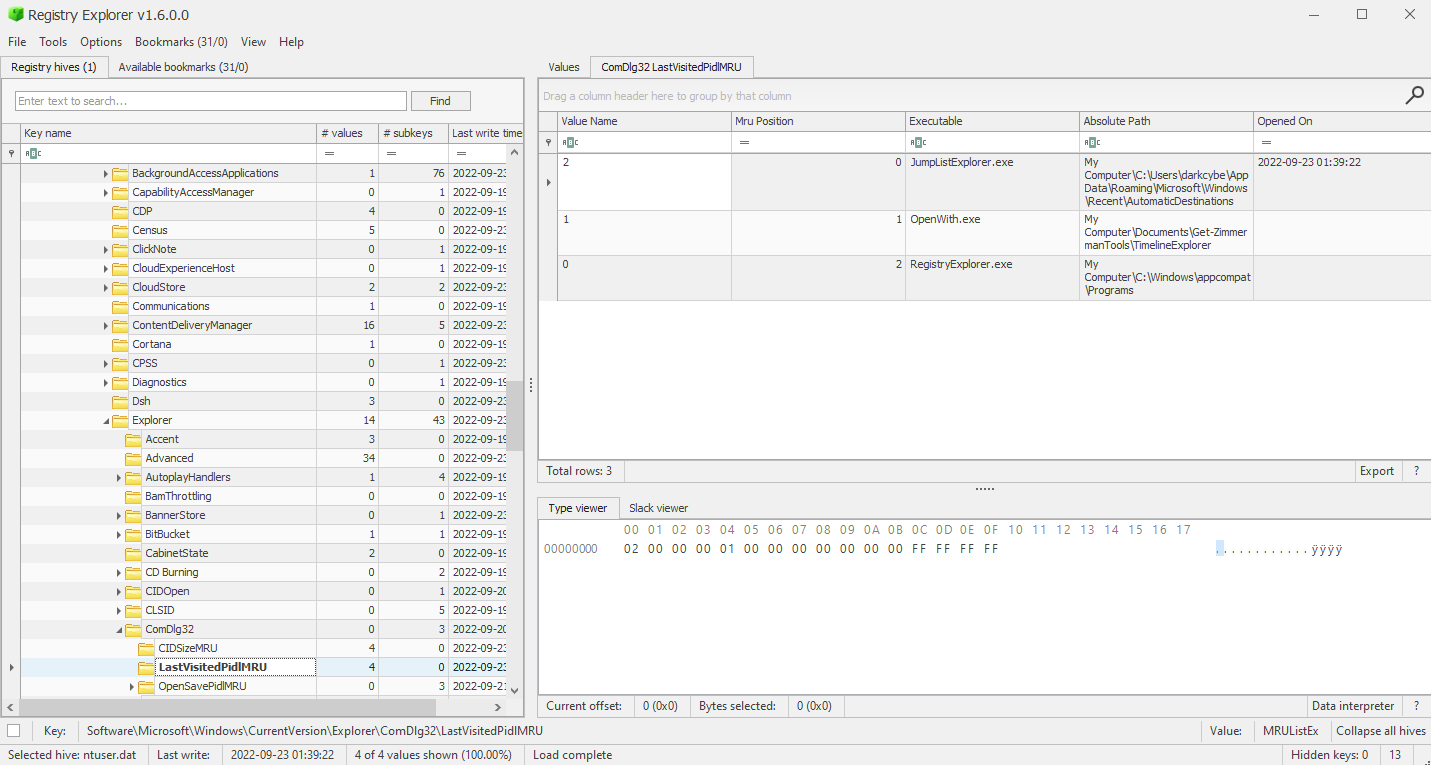
Parsing the ShimCache (AppCompatCache) for Evidence of Execution
Interesting Fields
- Program Name: Records the full executable filepath
- Modified Time: Date-time-group of last access time