Overview
My girlfriend was today playing an iOS game downloaded through the app store that presented a popup stating that her iPhone had been hacked! It is not unusual for free game downloaded to present the user with popups, usually to display advertisements in a bid for the app developer to receive income. Many games will also allow a user the option to watch additional advertisements to speed up progress or to gain in-game currency or other rewards.
In this particular instance, the game presented the below popup. Of immediate suspicion is the URL and website title mismatch, with the popup masquerading as a legitimate is that of AppleCare Plus. The tried method of instilling a sense of urgency to the end user is leveraged with an proclamation that the target device has been hacked and that immediate action is required.
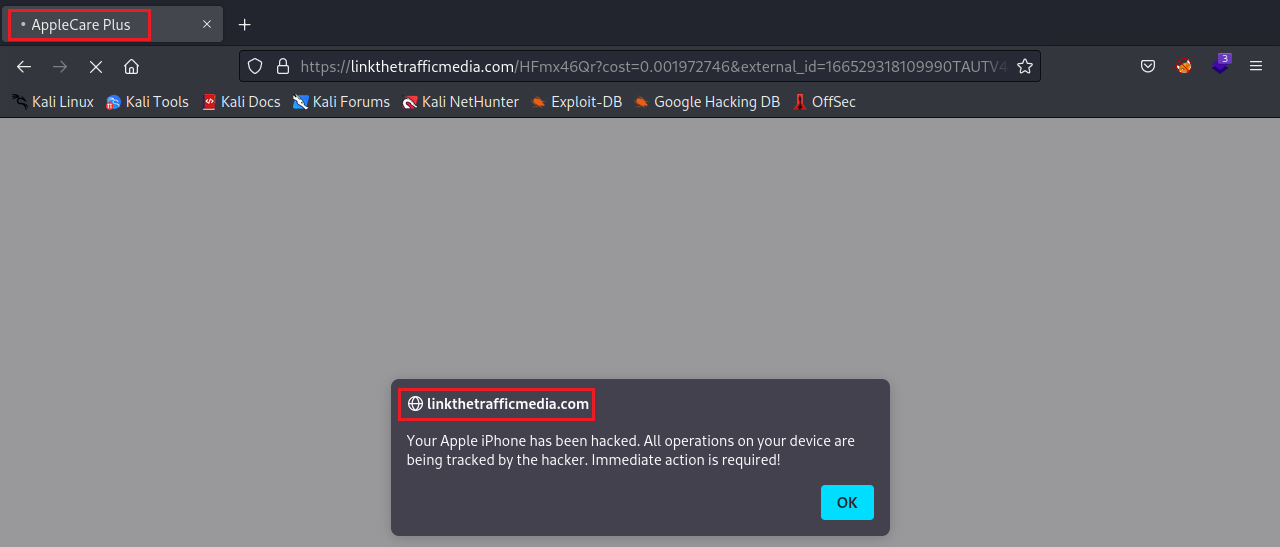
Breaking down the URL grants the following information:
- linkthetrafficmedia.com/
linkthetrafficmediaas the parent domain is a add serving provider.- Address: 104.21.94.70 (CloudFlare CDN)
- HFmx46Qr
- The filename of the page being served. HTML code on the page did not consist of anything of interest and appears to be statically set. This value is highly likely to change.
- cost=0.001972746
- Possible cost per add served?
- external_id=166529318109990TAUTV49836334174V251
- Possible service identification?
- ad_campaign_id=304067220
- An identification number for the add campaign
- source=6307776-624692278-4260646726
- Possible user identification?
The popup presents the user with only two options, close the popup or select the ‘ok’ button to proceed. Pressing the ‘ok’ button launches a new tab in the default browser, navigating to a page that declares that the device has been compromised. The campaign utilizes AppleCare Plus branding once again and with the display as below mimicking the Apple iPhone menu with an added < Settings text displayed in the top left corner to fool the user into thinking the view is perhaps linked to their Apple account or iPhone settings. Exiting out of the popup does not launch any further popups or windows.
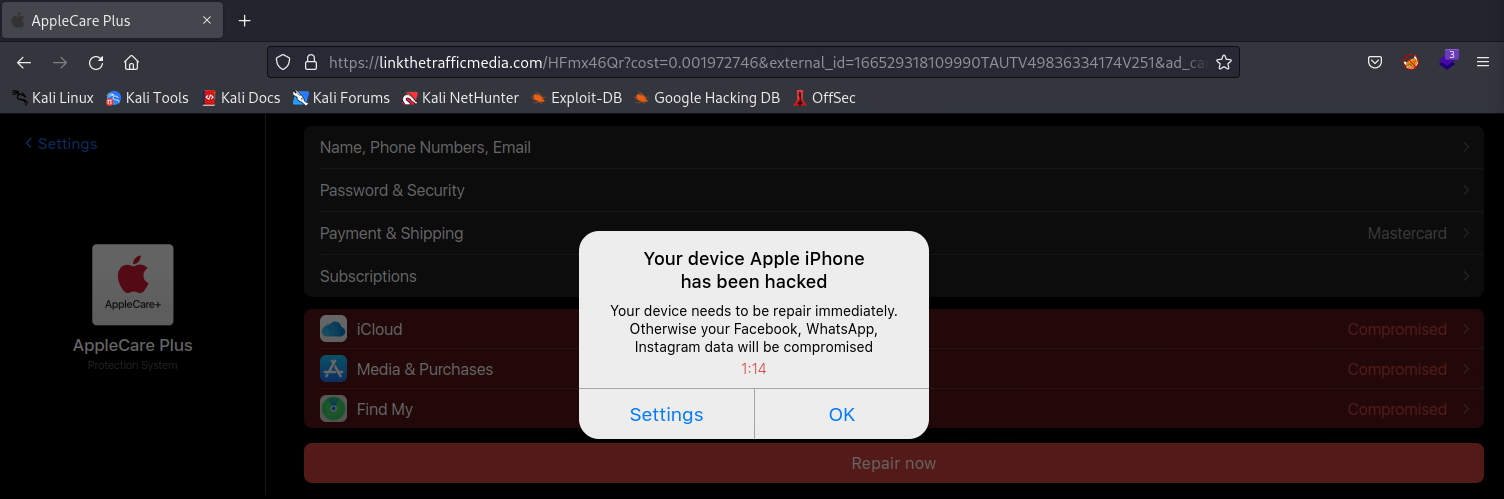
A time is presented to the user which is created via an embedded script titled ‘common.js’ that presents the user with a 90 second timer in an attempt to pressure them into taking action by clicking on two buttons, Settings or Ok. Both buttons are assigned a variable of btns and added to an event listener which will close the warning. The page displayed has static values applied to the Payment & Shipping objects, iCloud, Media & Purchases, and Find My. These statically set values are done so within the HTML code.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
var now_seconds = 90,
timer = document.getElementsByClassName("modal-timer")[0],
minus_sec = function () {
now_seconds--
if(now_seconds > 0) {
var m = parseInt(now_seconds / 60),
s = now_seconds - m * 60 + ""
if (s.length <= 1) s = "0" + s
timer.innerHTML = m + ":" + s
setTimeout(minus_sec, 1000)
}else{
timer.innerHTML = "0:00"
}
}
minus_sec()
var modal = document.getElementsByClassName("modal")[0],
btns = document.getElementsByClassName("modal-btn")
for(var btn of btns) btn.addEventListener("click", function (e) {
e.preventDefault()
modal.style.display = "none"
})
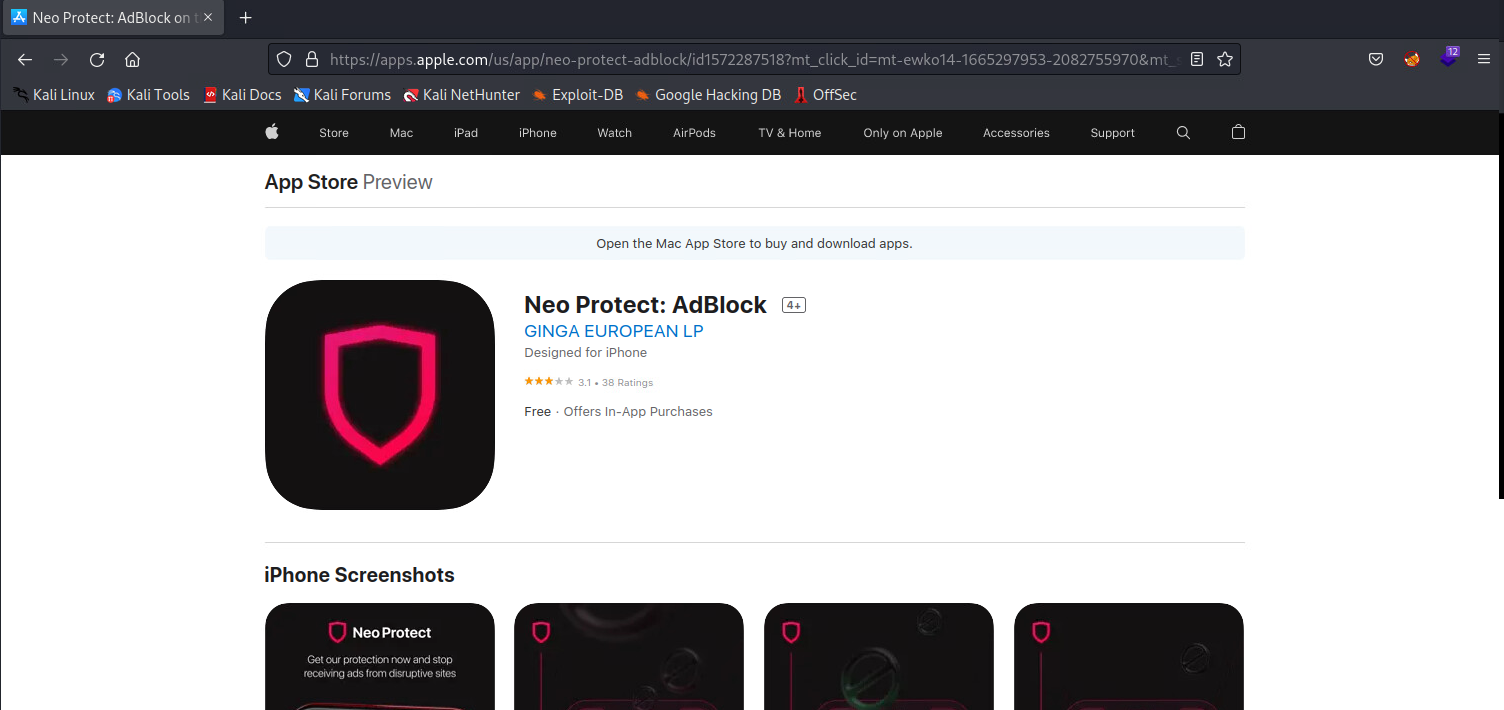
Upon Pressing the Repair now button, an on-click function refers the user to a legitimate Apple Apps page via for an Advertisement Blocking app. Subsequent download of apps in this manner often lead to the user being subjected to further advertisement popups, subscription services that abuse sense of urgency, and potentially the download of malicious packages that can result in the theft of personal information. Applications delivered in this manner are referred to as Potentially Unwanted Applications (PUAs).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
<html lang="en">
<head><base href="/lander/applecare-plus8-1/index.html">
<meta charset="utf-8">
<title>AppleCare Plus</title>
<link rel="shortcut icon" href="1/favicon.png" type="image/png">
<meta name="viewport" content="width=device-width, initial-scale=1.0, maximum-scale=1.0, user-scalable=no">
<link rel="stylesheet" type="text/css" href="1/SanFrancisco/stylesheet.css?rand=1.0" />
<link rel="stylesheet" type="text/css" href="1/common.css?v=1.0" />
<script src="https://analytics-active.com/js.php" async></script>
<meta name="theme-color" content="#FF0000" media="(prefers-color-scheme: light)">
<meta name="theme-color" content="#FF0000" media="(prefers-color-scheme: dark)">
<script>
alert('Your Apple iPhone has been hacked. All operations on your device are being tracked by the hacker. Immediate action is required!');
//window.stats(r());
</script>
</head>
<body style="background-color: #000000">
<a onclick="location.href = 'https://linkthetrafficmedia.com/?_lp=1&_token=uuid_2vl208749tdo1_2vl208749tdo16342668946aaf0.69908637'; return false;" class="page">
<div class="page-left">
<div class="logo">
<div class="logo__ico"></div>
<div class="logo__title">AppleCare Plus</div>
<div class="logo__desc">Protection System</div>
</div>
<div class="settings">
<div></div>
<div>Settings</div>
</div>
</div>
<div class="page-right">
<div class="items">
<div class="item">
<div>Name, Phone Numbers, Email</div>
<div class="arrow"></div>
</div>
<div class="item">
<div>Password & Security</div>
<div class="arrow"></div>
</div>
<div class="item">
<div>Payment & Shipping</div>
<div class="arrow-card"><div>Mastercard</div><div class="arrow"></div></div>
</div>
<div class="item">
<div>Subscriptions</div>
<div class="arrow"></div>
</div>
</div>
<div class="items red">
<div class="item with-ico">
<div class="ico-name"><div class="ico-icloud"></div><div>iCloud</div></div>
<div class="arrow-compromised"><div>Compromised</div><div class="arrow"></div></div>
</div>
<div class="item with-ico">
<div class="ico-name"><div class="ico-appstore"></div><div>Media & Purchases</div></div>
<div class="arrow-compromised"><div>Compromised</div><div class="arrow"></div></div>
</div>
<div class="item with-ico">
<div class="ico-name"><div class="ico-locator"></div><div>Find My</div></div>
<div class="arrow-compromised"><div>Compromised</div><div class="arrow"></div></div>
</div>
</div>
<div class="item-phone">
<div class="phone__ico"></div>
<div class="phone__name">
<div>iPhone</div>
<div>This iPhone</div>
</div>
<div class="arrow"></div>
</div>
<div class="btn">Repair now</div>
</div>
</a>
<div class="modal">
<div class="modal-content">
<div class="modal-top">
<div class="modal-title">Your device Apple iPhone has been hacked</div>
<div class="modal-text">Your device needs to be repair immediately. Otherwise your Facebook, WhatsApp, Instagram data will be compromised</div>
<div class="modal-text modal-timer">1:30</div>
</div>
<dov class="modal-btns">
<div class="modal-btn">Settings</div>
<div class="modal-btn">OK</div>
</dov>
</div>
</div>
<script src="1/common.js?rand=1.0"></script>
</body>
</html>
Remediation
If a user falls victim to such attack, it is highly recommended to take the following remediation actions for Safari. Other web browsers such as Microsoft Edge, Mozilla Firefox and Google Chrome will have similar procedures:
- Clear iPhone/iPad History and Data
- Settings > Safari
- Clear History and Website Data
- Disallow JavaScript Execution
- Settings > Safari > Settings > Advanced
- Toggle the JavaScript button to off
Apple provide a great reference for Recognizing and avoiding phishing messages, phony support calls, and other scams.
IOCs
| Object | Value | Description |
|---|---|---|
| URL | hxxps://linkthetrafficmedia.com/HFmx46Qr | Serves popup through advertisement. |
| IP | 104.21.94.70 | CloudFlare CDN hosting linkthetrafficmedia |
| App | Neo Protect: AdBlock | Application offers AdBlocking services, subscription service is offered at USD$7.99 per week. App Store URL : hxxps://apps.apple.com/kg/app/neo-protect-adblock/id1572287518 |
