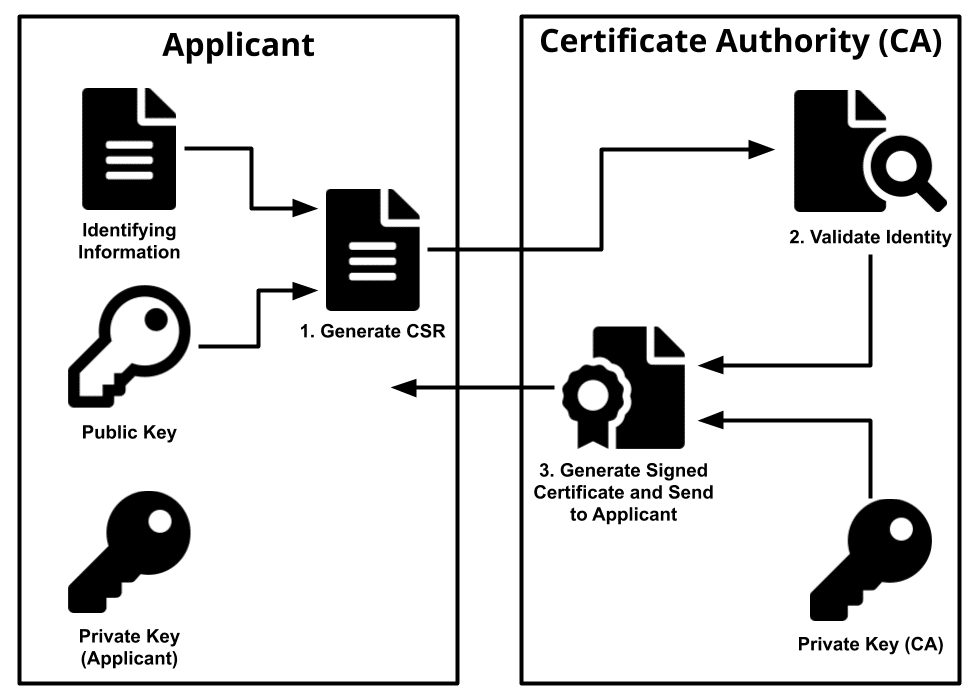
Overview
PKI implements two cryptographic methods to encrypt and decrypt traffic; symmetric and asymmetric cryptography and hashing. The purpose of establishing PKI encryption for network communications is to provide strong authentication schemes to protect data confidentiality and integrity, two of the core pillars of the CIA triad for ensuring that an environment is secured. Being a hybrid cryptographic method in the fact that PKI utilizes symmetric and asymmetric cryptography and hashing, it can harness the advantages of each to provide a robust, fast and effective encryption method.
Keys
The hybrid cryptographic implementation harnessed by PKI leverages the below;
- Symmetric: Utilizes a single key shared between two parties to encrypt and decrypt data. Faster, however less secure than asymmetric cryptography.
- Asymmetric: Consists of a private and public key pair, both are mathematically related however one cannot be derived from the other. Data is encrypted with the originators private key and recipients public key, with only the holder of the recipients private key being able to decrypt the data. More secure, however slower than symmetric cryptography.
- Hybrid: Generates a session key based on the symmetric cryptography method to validate communication between two parties and encrypts that session key using asymmetric cryptography, the originator encrypting the key with their private key and the recipients public key. Once the recipient decrypts the session key using their private key, the session key is then used securely to transfer encrypted data.
Algorithms, Hashing, and Standards
Symmetric and asymmetric employ different cryptographic algorithms to encrypt data, with certain algorithms develops to be used for each method and are not compatible with each other. The examples listed below are the current common implementations and do not list previous cryptographic algorithms that have been replaced.
- Symmetric: Advanced Encryption Standard (AES) - 128-bit block cypher. Contains keys of sizes: 128, 192, or 256 bits.
- Asymmetric: Rivest-Shamir-Adleman Standard (RSA) - Contains keys of sizes: 1024, 2048, or 4096 bits.
- Hashing: There are numerous amounts of different hashing algorithms that can be employed, however the most common for use in encrypting network data and Digital Certificates are:
- MD5: Message-Digest Algorithm, 128-bit hash value
- SHA-1: Secure Hash Algorithm 1, 160-bit hash value
- SHA-2: Secure Hash Algorithm 2, 224, 256, 384, or 512-bit hash value
- SHA-3: Secure Hash Algorithm 3, 224, 256, 384, or 512-bit hash value
- Standards: There are a number of different standards that PKI implementations can follow, however the most common and primary standard is the below. Other standard tend to be more industry or vendor specific:
- X.509: This standard defines the format of public key certificates that are used in many internet protocols including SSL/TLS, digital signatures and certificates.
Digital Certificates
Digital certificates are a large part of PKI. Digital certificates are a logical file formatted upon the X.509 standard and include information pertaining to an originators validity. Implementations of digital certificates vary, from digitally signing emails to ensure non-repudiation, code signing, and probably most visible in day-to-day usage is the use of digital certificates in SSL/TLS encryption. The details stored within a digital certificate vary, however some of the more useful are:
- Originators public key
- Originators identification details
- Issuing authority of the certificate (CA)
- Valid dates of use
Being a logical file, there are a number of different filetypes that will be encountered, such as;
- .pem: Privacy Enhanced Email
- .cer, .crt, .der: Certificate files
- .p12: PKCS#12. Usually contains X.509 certificates, public, and private keys and is password protected.
- .csr: Certificate Signing Request. Contains information submitted by an originator requesting a certificate.
Digital certificates are issued by Certificate Authorities (CA), who are responsible for proving the authenticity of the individual or organization of whom issued the request for the certificate. There are numerous trusted commercial CAs, such as Digicert, Let Encrypt, and Comodo to name a few. Organization can also implement their own internal CA for certificates being used within the network boundaries of their environment.
Generating a Private Key and CSR with OpenSSH v3
OpenSSL are a project team who develop and maintain software that allows the creation of general-purpose PKI keys and certificates. The below example depicts the steps required to create a RSA 2048-bit private key and CSR file.
- Download the OpenSSL software from the OpenSSL Github Repo, download and installation guides are available for different Operating Systems.
- Generate a CSR and private key in order to apply for a CA signed certificate, required parameters will be prompted during the execution of the command, including:
- Country Name
- State or Province Name
- Locality Name
- Organization Name
- Organizational Unit Name
- Common Name
- Email Address
- A Challenge Password
1
openssl req -newkey rsa:2048 -noenc -keyout <private key name>.key -out <CSR name>.csr
Generating a Private Key and Self-Signed Certificate with OpenSSH V3
OpenSSL also allows users to create self-signed certificates that are intended for use within a private network, having not been signed by a validated CA. The below example depicts the steps required to create a RSA 2048-bit private key and CRT file that is valid for 825 days.
- Download the OpenSSL software from the OpenSSL Github Repo, download and installation guides are available for different Operating Systems.
Generate a private key and generate a certificate
1
openssl req -newkey rsa:2048 -noenc -keyout <private key name>.key -x509 -days 825 -out <certificate name>.crt