Overview
PowerShell-Empire is a post-exploitation framework that is built upon a large collection of PowerShell modules and scripts. It also contains various scripts written in C# and Python that can be used against a target OS. The PowerShell-Empire framework currently has hundreds of modules that can aid in almost all penetration testing tactics and techniques.
PowerShell-Empire have also developed a front-end GUI called Starkiller for the framework which makes configuration and activities that little bit easier to manage, especially when dealing with multiple targets. However, there is still the CLI available, with the framework running a server/client model.
Kali Linux comes with PowerShell-Empire and Starkiller pre-installed. 1
| Tool Name | Version | MITRE ATT&CK Tactic | MITRE ATT&CK Technique |
|---|---|---|---|
| PowerShell-Empire | V4.8.0 | Credential Access Privilege Escalation Discovery Collection Command and Control Exfiltration Execution Persistence Defense Evasion Lateral Movement |
Starting PowerShell-Empire with Starkiller on Kali Linux
Start the PowerShell-Empire Server and Client in separate terminal windows. Ensure that the server is operational prior to starting the client to ensure that they can communicate.
1 2
sudo powershell-empire server sudo powershell-empire client
Create a new user on the PowerShell-Empire Client. Once the new user has been created, the PowerShell-Empire Client terminal can be closed if using the Starkiller GUI, otherwise the client is the interface to be used for configuring and interacting with agents.
1 2
(Empire) > admin (Empire) > create_user %USERNAME% %PASSWORD%
Open Starkiller and logon using the credentials set in the previous section. The URL by default is set to
https://localhost:1337.
Adding a Listener through Starkiller
- Navigate to the Listener window
- Press the
createbutton on the top right to enter the New Listener prompt and select the type of listener using the drop-down menu. For this example, the
HTTP Listeneris selected. Configure the Listener as below:1 2 3
Name: darkcybeHttp Host: 172.16.2.2 Port: 1335
- Press
submitto initiate the HTTP Listener
Additional configuration can be set, such as:
- KillDate: An expiration date that sets agent autocleanup
- DefaultProfile: Sets the URL GET request parameters to blend into normal traffic
- UserAgent: Set the UA string, useful to masquerade traffic
- ServerVersion: Set to a common Server Header to masquerade traffic
Adding a Stager through Starkiller
- Navigate to the Stager window
- Press the
createbutton on the top right to enter the New Stager prompt and select the type of stager using the drop-down menu. For this example, the
windows/reverseshellis selected. Configure the Stager as below:1 2
Listener: darkcybeHttp LocalHost: 172.16.2.2
- Press
submitto create the stager. The stager can then be downloaded and transferred to the target host.
Payloads can be created for Windows, MacOs, and Linux.
Interacting with Agents through Starkiller
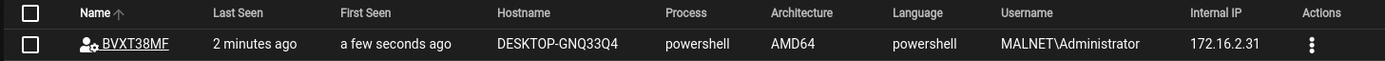
When a target executes the stager, the agent will connect to the Listener and be displayed on the Agents window, as per the image below:
![PowerShell Empire - Agents PowerShell Empire - Agents]()
Selecting the agent will open an agent specific window containing a number of different options:
- Interact: Allows for shell commands and PowerShell-Empire Modules to be executed on the agent.
- File Browser: Directory traversal including file upload and download functionality.
- Tasks: A history of actions carried out on the host
- View: Agent specific configuration
PowerShell-Empire Modules
Discovery Modules
When executing the Bloodhound modules, the Sharphound archive defaults to C:\Users\%USERNAME%\ on the target agent. The download directory on the attacking Kali host is /var/lib/powershell-empire/server/downloads/%AGENT%/.
| Action | Module | Configuration |
|---|---|---|
| Find a Domain Controller | powershell/situational_awareness/network/powerview/get_domain_controller | |
| Identify Antivirus | powershell/situational_awareness/host/antivirusproduct | |
| Bloodhound AD Scanning | powershell/situational_awareness/network/bloodhound3 |
Credential Access Modules
Using the Mimkatz LogonPasswords modules automatically adds collected credentials to the credentials window within PowerShell-Empire.
| Action | Module | Configuration |
|---|---|---|
| Mimkatz Password Dump | powershell/credentials/mimikatz/logonpasswords | |
| Browser Credential Dump | powershell/collection/FoxDump powershell/collection/ChromeDump | |
| Responder/Inveigh LLMNR Abuse | powershell/collection/inveigh |
Lateral Movement Modules
| Action | Module | Configuration |
|---|---|---|
Privilege Escalation Modules
| Action | Module | Configuration |
|---|---|---|
| Get SYSTEM Privileges | powershell/privesc/getsystem | |
| Search for Privesc Vulnerabilities | powershell/privesc/sherlock powershell/privesc/powerup/allchecks |